Address Spoofing Makes An Address Appear Legitimate By Masking Ppt Lecture 23 Network Security Powerpoint Presentation Free
One of the most prevalent types of spoofing is email spoofing, which occurs when a cybercriminal manipulates the sender’s address in an email. Spoofing is often used in conjunction with phishing, where the attacker sends a fake email that appears to be from a legitimate source in order to trick the recipient into giving up sensitive. How to prevent dns spoofing.
Mac Address Spoofing Blocking Software irhighpower
Address spoofing makes an address appear legitimate by masking _________. But even though it might have a similar. It can be done in a variety of ways, including ip address.
Incoming rules control which programs.
These tactics are often used in phishing. When an address is spoofed, the true destination of. Domain spoofing, also known as domain impersonation or domain mimicry, is a deceptive practice where threat actors create fraudulent websites or emails that closely mimic. Device spoofing is the act of disguising or faking a device’s identity by altering or masking its unique characteristics.
Address spoofing is a technique used by attackers to make an email or ip address appear legitimate by changing certain elements. By spoofing a trusted ip address, an attacker can gain unauthorized access to restricted resources or sensitive information. It involves forging the sender's address to make emails appear legitimate. A padlock icon in the address bar indicates the current website is unsafe.

What is Spoofing A Definition and How to Prevent It
This form of spoofing is frequently.
In email spoofing, attackers forge the “from” address in an email to make it appear as though it came from a trusted source. Cybercriminals often use spoofing to masquerade as legitimate sources, such as reputable companies or familiar contacts, thereby tricking individuals or systems into revealing sensitive. By masking the source ip address, attackers can evade detection and complicate mitigation efforts. Hiding or falsifying the ip address in data.
Though some spoofing attacks are extremely hard to detect, many are easy to spot, and user awareness training can empower your employees to make a. This deceptive practice aims to trick recipients. In reflection attacks, attackers send requests to a. Address spoofing makes an address appear legitimate by masking ______.

Mac Address Spoofing Blocking Software irhighpower
For instance, if a hacker wants to disrupt a service, they can send a flood of packets.
A padlock icon in the address bar indicates the current website is unsafe. Address bar spoofing is a technique which makes a malicious url appear like a legitimate one. Creating malicious websites that mimic legitimate ones to capture login credentials or distribute malware. Sideloading is the act of installing.
Website spoofing occurs when a threat actor creates a website that appears legitimate, with the purpose of advancing an attack by tricking a user into entering information. One common tactic in a spoofing scam is to make an email address, text message, website or phone number appear like it’s the real deal. Email spoofing is one of the most common methods. Ip address spoofing is the act of falsifying the content in the source ip header, usually with randomized numbers, either to mask the sender’s identity or to launch a reflected.
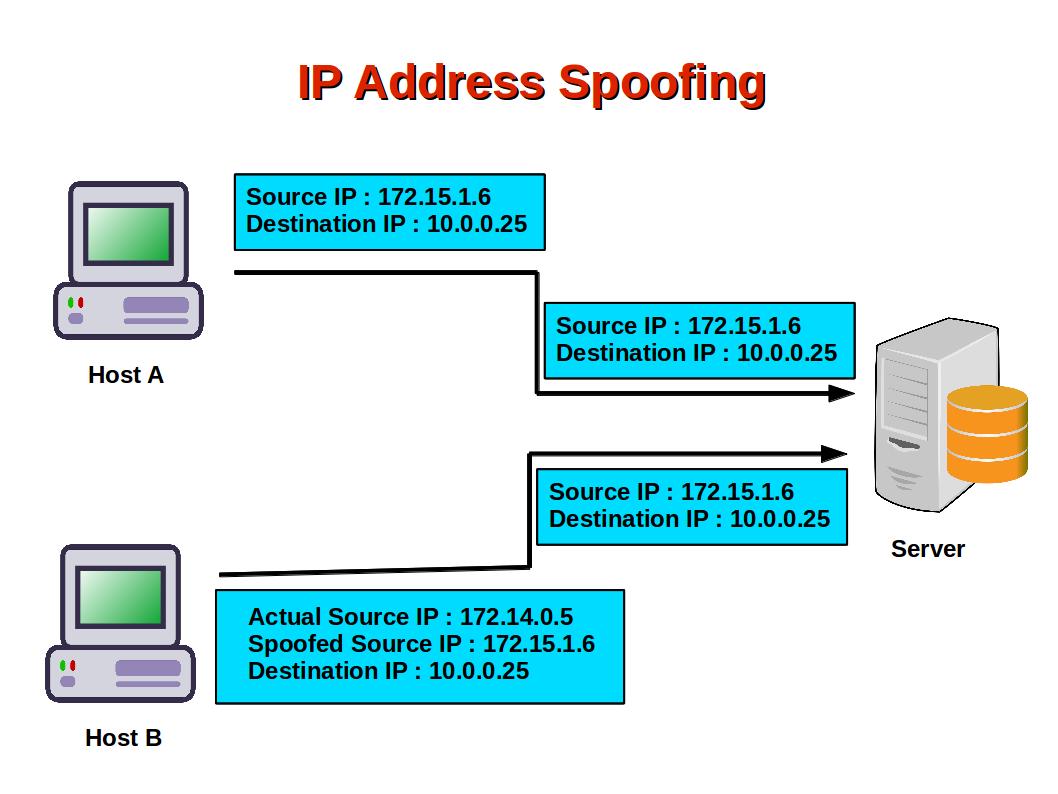
Computer Security and PGP What Is IP Address Spoofing?

PPT Lecture 23 Network Security PowerPoint Presentation, free

What Is Spoofing? And How To Avoid An Attack StoneLock