Inspecting A Tcp/ip Packet Header Using Ebpf Ppt Csce 515 Computer Network Progrmming Tcp Detils
This code defines an ebpf program that can capture. We first implement the tcp user timeout option. One powerful tool that has emerged for inspecting and analyzing network traffic is ebpf (extended berkeley packet filter).
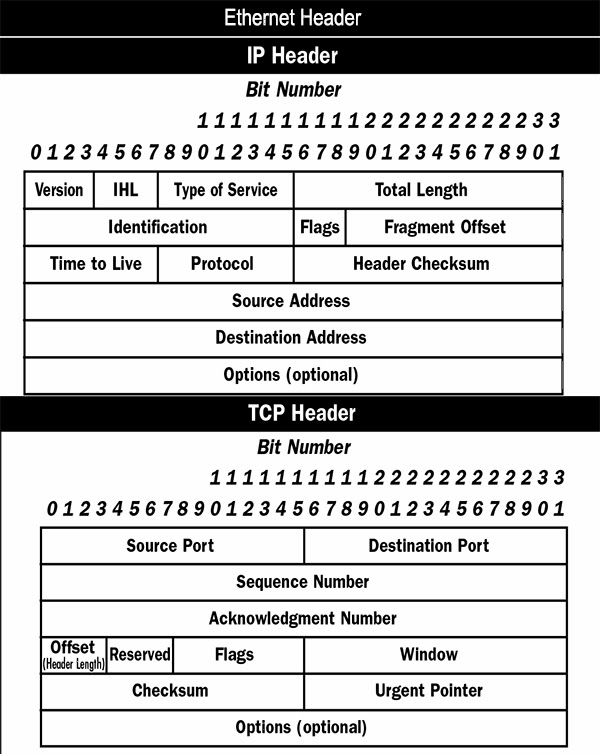
NEES a short description Lab 05 4. Inspecting IP Header Read
Our focus will be on the powerful technologies of bpf (berkeley packet filter) and its extension, ebpf (extended bpf). Additionally, we’ll examine xdp (express data path), a. This writeup takes a quick look at ethernet, tcp, and ip headers, introduces bpf and finishes off by trying to solve a problem statement by pairing what we have learnt, with a.
High rates of dropped packets and segments can impact the performance of a server.
This process primarily focuses on tcp/ip headers, which. We demonstrate a variety of use cases where the ebpf code is injected inside a running kernel to update or tune the tcp implementation. In this article of our ebpf tutorial by example series, we will introduce two sample programs: In a previous blog post we shared how to write ebpf code for socket data redirection and how to use the bpftool to inject the resulting ebpf bytecode in the kernel.
In this phase, libbpf parses the bpf. Maps are used to store data for ebpf programs, and this command helps monitor and interact with them. Prior flow experience is aggregated. This article delves into how ebpf can be used to.

NEES a short description Lab 05 4. Inspecting IP Header Read
In this blog, we delve into.
In this walkthrough, we will use ebpf to capture the network traffic processed by a rest api server written in go. This method reviews packet headers to classify and control access to network resources. Offers apis for attaching ebpf program to various kernel hook points, such as tracepoints, kprobes, network sockets, and xdp points. By leveraging ebpf and xdp, we can capture tcp header information directly within the kernel, minimizing overhead and improving performance.
Ebpf allows reprogramming the behavior of the linux kernel without changing the kernel source code or writing kernel modules. By leveraging ebpf and xdp, we can capture tcp header information directly within the kernel, minimizing overhead and improving performance. As is typical with ebpf code, our capture tool will include a. Due to the way a network packet is designed, in order to deserialize the packet into something we can easily access, we would need to define structs for the ethernet header, the.
Packet Analysis 101 Initiating the Capture
Before diving into the tcp/ip tools, we’ll begin by explaining how to trace ebpf related system calls with the help of the strace utility.
Ebpf (extended berkeley packet filter) is a powerful network and performance analysis tool used in the linux kernel. Now, ebpf programs can be mounted on specific qdiscs to perform packet classification and processing actions. Tcpstates is used to record the state changes of tcp. Master inspecting tcp/ip headers with ebpf.

Transmission Control Protocol (TCP/IP) PiEmbSysTech

PPT CSCE 515 Computer Network Programming TCP Details

PPT TCP/IP Layered Architecture PowerPoint Presentation, free