Which Of The Following Is A Concern About Ec Encryption Common Types Protocols Nd Lgorithms Explined
This is generally a positive aspect of ec encryption, not a concern. Which of the following is a type of encryption that has two different keys? The question asks about concerns related to elliptic curve (ec) encryption.
ECES ECCouncil Certified Encryption Specialist Test Questions and
Post any question and get expert help quickly. Which of the following is a type of encryption that has two different keys. The concern about ec encryption is that it is vulnerable to quantum computing attacks, unlike aes encryption, which is not mentioned as a concern.
Study with quizlet and memorize flashcards containing terms like how did the atbash cipher work?, des has a key space of what?, which of the following are valid key sizes for aes.
It is weaker than more traditional encryption like aes. Public key encryption enables parties to initiate secure communications through an open medium, such as the internet, in which there might be eavesdroppers. One key can encrypt the message and the other key can only decrypt it. Ec the us nist recommends using ec encryption, and the nsa allows its use to protect top secret data with 384 bit ec keys.
Not the question you’re looking for? Which of the following is a concern about ec encryption? Not the question you’re looking for? It is weaker than more traditional encryption like aes.

What is CRYPTOGRAPHY and Types or Encryption? Free Learning Tech
One key can encrypt the message and the other key can only decrypt it?
Robust hardware and software support. Here’s the best way to solve it. A) symmetric b) asymmetric c) block cipher d). The main advantage of elliptic curve encryption (ecc) over.
The primary concerns about ec encryption include complex key management and potential vulnerabilities to quantum computing attacks, while it is not inherently weaker than. Show more… the question asks about concerns related to elliptic curve. Anyone, including the messaging service, can see the public key, but only one person knows the. The concern about ec encryption is vulnerability t.
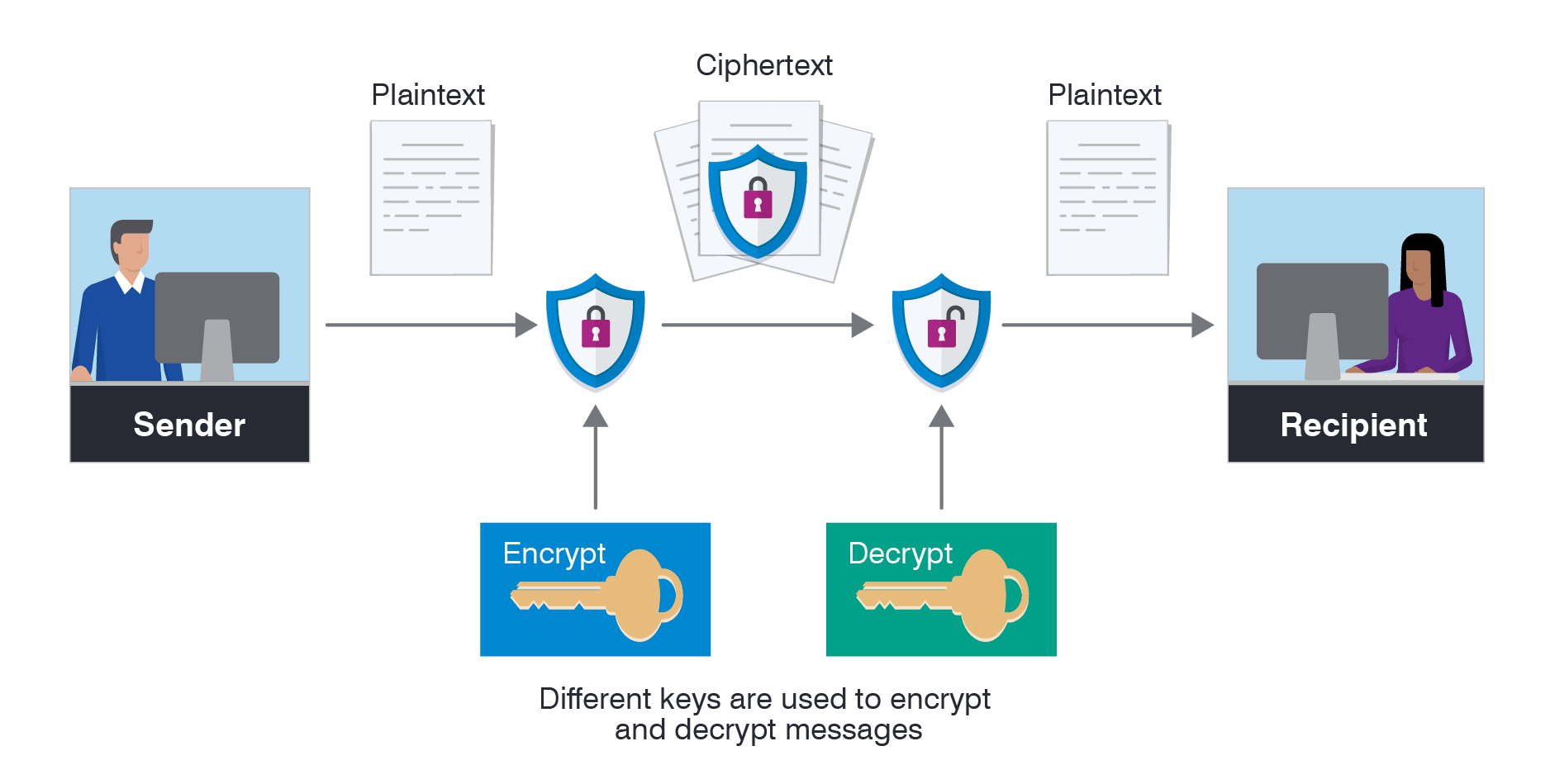
What Is Encryption? Definition, Types & More Proofpoint US
But, the nsa has expressed concern about ec encryption.
A public and a private key. Public key encryption employs two keys: The first option, robust hardware and software support, is generally not a concern, as ec encryption is. Here’s the best way to solve it.
A concern about ec encryption is that it may be vu. Public key encryption is not. Which of the following is an advantage of elliptic curve encryption over rsa encryption? While key management can be complex in.

ECES ECCouncil Certified Encryption Specialist Test Questions and

Common Encryption Types, Protocols and Algorithms Explained

What Is Encryption and Do You Need It? Panda Security Mediacenter